Endpoint protector
 Having the possibility to control device activity inside a network from a simple
Web interface will make things easier for you. Strong device use policies will
ensure proactive protection for a safer working environment.
Having the possibility to control device activity inside a network from a simple
Web interface will make things easier for you. Strong device use policies will
ensure proactive protection for a safer working environment.
 Offers detailed control over sensitive data leaving the company’s network. Through
efficient content inspection, transfers of important company documents will be
logged, reported and blocked.
Offers detailed control over sensitive data leaving the company’s network. Through
efficient content inspection, transfers of important company documents will be
logged, reported and blocked.
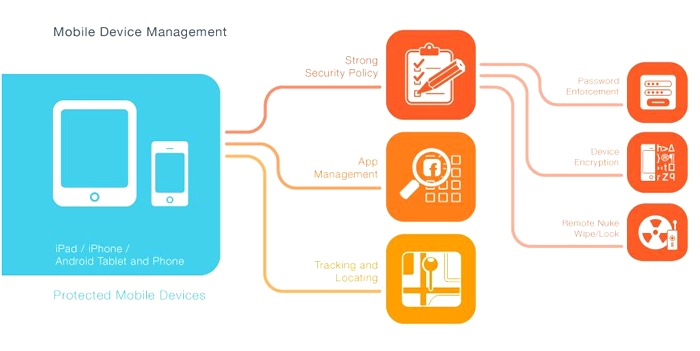
 Offers enhanced control over the use of Android and iOS smartphones and tablets by
companies’ employees, enforcing strong security policies and detailed tracking of
all mobile devices.
Offers enhanced control over the use of Android and iOS smartphones and tablets by
companies’ employees, enforcing strong security policies and detailed tracking of
all mobile devices.
 To learn more details, please contact us.
To learn more details, please contact us.

 Engish
Engish 繁體中文
繁體中文 簡體中文
簡體中文